As a reminder all Enrollment Management department mailboxes (Outlook) were migrated to Office 365 overnight (https://its.wsu.edu/o365-outlook-migration). If you or a coworker are having problems logging in please try using your email address (NID@wsu.edu) as opposed to domain (ad\NID) for user name. Also don’t forget to check portable devices such as cell phones and tablets.
Known issues after migration:
- Some people may have issues with various Permissions they have set for others, or Permissions other people may have set for them.
- If people can see other people’s Calendars, the details may not be visible (only Free-Busy status is showing) until everyone has moved to the new system.
- In many cases, Outlook caches E-Mail addresses for people you frequently correspond with. These cached addresses may have to be purged – they are part of the Outlook Auto-Correct Name List.
The settings we believe you may have to re-establish with your Office 365 Mailbox include
- Signature Blocks
- Distribution Lists
- If you assigned permissions for an AD Group to access your mailbox or calendar, these groups may not migrate as-is to Office 365. So you may need to re-establish the permissions for sharing on an individual basis, not a group.
Please contact EIT if you are still having issues, https://em.wsu.edu/eit/help.
=====================================================
What is a social engineering attack?
In a social engineering attack, an attacker uses human interaction (social skills) to obtain or compromise information about an organization or its computer systems. An attacker may seem unassuming and respectable, possibly claiming to be a new employee, repair person, or researcher and even offering credentials to support that identity. However, by asking questions, he or she may be able to piece together enough information to infiltrate an organization's network. If an attacker is not able to gather enough information from one source, he or she may contact another source within the same organization and rely on the information from the first source to add to his or her credibility.
What is a phishing attack?
Phishing is a form of social engineering. Phishing attacks use email or malicious websites to solicit personal information by posing as a trustworthy organization. For example, an attacker may send email seemingly from a reputable credit card company or financial institution that requests account information, often suggesting that there is a problem. When users respond with the requested information, attackers can use it to gain access to the accounts.
Phishing attacks may also appear to come from other types of organizations, such as charities. Attackers often take advantage of current events and certain times of the year, such as
- natural disasters (e.g., Hurricane Katrina, Indonesian tsunami)
- epidemics and health scares (e.g., H1N1)
- economic concerns (e.g., IRS scams)
- major political elections
- holidays
How do you avoid being a victim?
- Be suspicious of unsolicited phone calls, visits, or email messages from individuals asking about employees or other internal information. If an unknown individual claims to be from a legitimate organization, try to verify his or her identity directly with the company.
- Do not provide personal information or information about your organization, including its structure or networks, unless you are certain of a person's authority to have the information.
- Do not reveal personal or financial information in email, and do not respond to email solicitations for this information. This includes following links sent in email.
- Don't send sensitive information over the Internet before checking a website's security.
- Pay attention to the URL of a website. Malicious websites may look identical to a legitimate site, but the URL may use a variation in spelling or a different domain (e.g., .com vs. .net).
- If you are unsure whether an email request is legitimate, try to verify it by contacting the company directly. Do not use contact information provided on a website connected to the request; instead, check previous statements for contact information. Information about known phishing attacks is also available online from groups such as theAnti-Phishing Working Group.
- Install and maintain anti-virus software, firewalls, and email filters to reduce some of this traffic.
- Take advantage of any anti-phishing features offered by your email client and web browser.
What do you do if you think you are a victim?
- If you believe you might have revealed sensitive information about your organization, report it to the appropriate people within the organization, including network administrators. They can be alert for any suspicious or unusual activity.
- If you believe your financial accounts may be compromised, contact your financial institution immediately and close any accounts that may have been compromised. Watch for any unexplainable charges to your account.
- Immediately change any passwords you might have revealed. If you used the same password for multiple resources, make sure to change it for each account, and do not use that password in the future.
- Watch for other signs of identity theft. Consider reporting the attack to the police, and file a report with theFederal Trade Commission.
Is identity theft just a problem for people who submit information online?
You can be a victim of identity theft even if you never use a computer. Malicious people may be able to obtain personal information (such as credit card numbers, phone numbers, account numbers, and addresses) by stealing your wallet, overhearing a phone conversation, rummaging through your trash (a practice known as dumpster diving), or picking up a receipt at a restaurant that has your account number on it. If a thief has enough information, he or she may be able to impersonate you to purchase items, open new accounts, or apply for loans.
The Internet has made it easier for thieves to obtain personal and financial data. Most companies and other institutions store information about their clients in databases; if a thief can access that database, he or she can obtain information about many people at once rather than focus on one person at a time. The Internet has also made it easier for thieves to sell or trade the information, making it more difficult for law enforcement to identify and apprehend the criminals.
How are victims of online identity theft chosen?
Identity theft is usually a crime of opportunity, so you may be victimized simply because your information is available. Thieves may target customers of certain companies for a variety of reasons; for example, a company database is easily accessible, the demographics of the customers are appealing, or there is a market for specific information. If your information is stored in a database that is compromised, you may become a victim of identity theft.
Are there ways to avoid being a victim?
Unfortunately, there is no way to guarantee that you will not be a victim of online identity theft. However, there are ways to minimize your risk:
- Do business with reputable companies– Before providing any personal or financial information, make sure that you are interacting with a reputable, established company. Some attackers may try to trick you by creating malicious web sites that appear to be legitimate, so you should verify the legitimacy before supplying any information.
- Take advantage of security features– Passwords and other security features add layers of protection if used appropriately.
- Check privacy policies– Take precautions when providing information, and make sure to check published privacy policies to see how a company will use or distribute your information. Many companies allow customers to request that their information not be shared with other companies; you should be able to locate the details in your account literature or by contacting the company directly.
- Be careful what information you publicize– Attackers may be able to piece together information from a variety of sources. Avoid posting personal data in public forums.
- Use and maintain anti-virus software and a firewall– Protect yourself against viruses and Trojan horses that may steal or modify the data on your own computer and leave you vulnerable by using anti-virus software and a firewall. Make sure to keep your virus definitions up to date.
- Be aware of your account activity– Pay attention to your statements, and check your credit report yearly. You are entitled to a free copy of your credit report from each of the main credit reporting companies once every twelve months.
How do you know if your identity has been stolen?
Companies have different policies for notifying customers when they discover that someone has accessed a customer database. However, you should be aware of changes in your normal account activity. The following are examples of changes that could indicate that someone has accessed your information:
- unusual or unexplainable charges on your bills
- phone calls or bills for accounts, products, or services that you do not have
- failure to receive regular bills or mail
- new, strange accounts appearing on your credit report
- unexpected denial of your credit card
What can you do if you suspect or know that your identity has been stolen?
Recovering from identity theft can be a long, stressful, and potentially costly process. Many credit card companies have adopted policies that try to minimize the amount of money you are liable for, but the implications can extend beyond your existing accounts. To minimize the extent of the damage, take action as soon as possible:
- Start by visiting IdentityTheft.gov –This is a trusted, one-stop resource to help you report and recover from identity theft. Information provided here includes checklists, sample letters, and links to other resources.
- Possible next steps in the process –You may need to contact credit reporting agencies or companies where you have accounts, file police or other official reports, and consider other information that may have been compromised.
==================================================================================
The Internal Revenue Service (IRS) has released an alert warning of various types of scams targeting taxpayers this summer.
IR-2017-112, June 26, 2017
WASHINGTON – The Internal Revenue Service today issued a warning that tax-related scams continue across the nation even though the tax filing season has ended for most taxpayers. People should remain on alert to new and emerging schemes involving the tax system that continue to claim victims.
“We continue to urge people to watch out for new and evolving schemes this summer,” said IRS Commissioner John Koskinen. “Many of these are variations of a theme, involving fictitious tax bills and demands to pay by purchasing and transferring information involving a gift card or iTunes card. Taxpayers can avoid these and other tricky financial scams by taking a few minutes to review the tell-tale signs of these schemes.”
EFTPS Scam
A new scam which is linked to the Electronic Federal Tax Payment System (EFTPS) has been reported nationwide. In this ruse, con artists call to demand immediate tax payment. The caller claims to be from the IRS and says that two certified letters mailed to the taxpayer were returned as undeliverable. The scammer then threatens arrest if a payment is not made immediately by a specific prepaid debit card. Victims are told that the debit card is linked to the EFTPS when, in reality, it is controlled entirely by the scammer. Victims are warned not to talk to their tax preparer, attorney or the local IRS office until after the payment is made.
“Robo-call” Messages
The IRS does not call and leave prerecorded, urgent messages asking for a call back. In this tactic, scammers tell victims that if they do not call back, a warrant will be issued for their arrest. Those who do respond are told they must make immediate payment either by a specific prepaid debit card or by wire transfer.
Private Debt Collection Scams
The IRS recently began sending letters to a relatively small group of taxpayers whose overdue federal tax accounts are being assigned to one of four private-sector collection agencies. Taxpayers should be on the lookout for scammers posing as private collection firms. The IRS-authorized firms will only be calling about a tax debt the person has had – and has been aware of – for years. The IRS would have previously contacted taxpayers about their tax debt.
Scams Targeting People with Limited English Proficiency
Taxpayers with limited English proficiency have been recent targets of phone scams and email phishing schemes that continue to occur across the country. Con artists often approach victims in their native language, threaten them with deportation, police arrest and license revocation among other things. They tell their victims they owe the IRS money and must pay it promptly through a preloaded debit card, gift card or wire transfer. They may also leave “urgent” callback requests through phone “robo-calls” or via a phishing email.
Tell Tale Signs of a Scam:
The IRS (and its authorized private collection agencies) will never:
- Call to demand immediate payment using a specific payment method such as a prepaid debit card, gift card or wire transfer. The IRS does not use these methods for tax payments. The IRS will usually first mail a bill to any taxpayer who owes taxes. All tax payments should only be made payable to the U.S. Treasury and checks should never be made payable to third parties.
- Threaten to immediately bring in local police or other law-enforcement groups to have the taxpayer arrested for not paying.
- Demand that taxes be paid without giving the taxpayer the opportunity to question or appeal the amount owed.
- Ask for credit or debit card numbers over the phone.
For anyone who doesn’t owe taxes and has no reason to think they do:
- Do not give out any information. Hang up immediately.
- Contact the Treasury Inspector General for Tax Administration to report the call. Use theirIRS Impersonation Scam Reporting web page. Alternatively, call 800-366-4484.
- Report it to the Federal Trade Commission. Use theFTC Complaint Assistant on FTC.gov. Please add "IRS Telephone Scam" in the notes.
For anyone who owes tax or thinks they do:
- View tax account information onlineat IRS.gov to see the actual amount you owe. Then review payment options.
- Call the number on the billing notice, or
- Call the IRS at 800-829-1040. IRS workers can help
How to Know It’s Really the IRS Calling or Knocking
The IRS initiates most contacts through regular mail delivered by the United States Postal Service. However, there are special circumstances in which the IRS will call or come to a home or business, such as:
- when a taxpayer has an overdue tax bill,
- to secure a delinquent tax return or a delinquent employment tax payment, or,
- to tour a business as part of an audit or during criminal investigations.
Even then, taxpayers will generally first receive several letters (called “notices”) from the IRS in the mail. For more information, visit “How to know it’s really the IRS calling or knocking on your door” on IRS.gov.
Be safe out there!
=========================================
WSU Pullman ITS is migrating to Level3, WSU’s new local and long distance phone service provider. As part of this migration, there will be changes implemented on the campus phone system throughout this week (June 27 through June 30). We will be working with the new provider to implement all necessary changes and finalize the migration.
There should be no impact to 911 calling or statewide 5-digit dialing between WSU Pullman and the other WSU sites around the state during this transition. If there are problems or issues, Information Technology Services’ implementation team will work identify and resolve all issues as quickly as possible. Additionally, the changes are scheduled to take place after normal business hours to minimize impact to campus users.
Please contact your CougTech Help Desk (cougtech@wsu.edu or 509-335-4357) with any questions or concerns.
Thank you for your patience during this transition.
=========================================
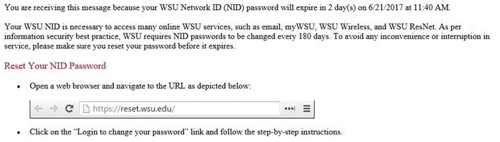
We have received word from ITS that NID services used to create a new NID or FID, or to reset a password for a current NID or FID, will be unavailable for the duration of the upgrade to CS 9.2. If you have received a notice recently to reset your NID password (see below), please be aware that you will be unable to do so starting Friday, June 30, at 10PM, through late in the day on Monday, July 3, when the upgrade completes.
Below is an example of the email sent to you when your NID password is ready to expire. The email is typically sent for 14 days. If you are currently in the 14 day window, we recommend that you reset your password prior to the upgrade. If you do not change it prior to the upgrade, you will need to wait until after July 3.
If you have questions or need assistance, please feel free to email the helpdesk: eit.helpdesk@wsu.edu
=========================================
Construction started on the Grimes Way play field parking lot Monday, June 5, adding more parking stalls. The parking lot will be closed to vehicle parking until mid-July.
=========================================
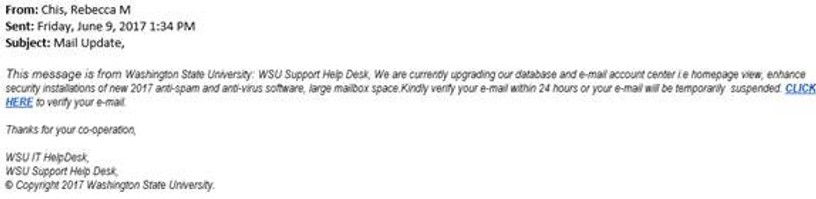
Please delete if you receive this.
=========================================
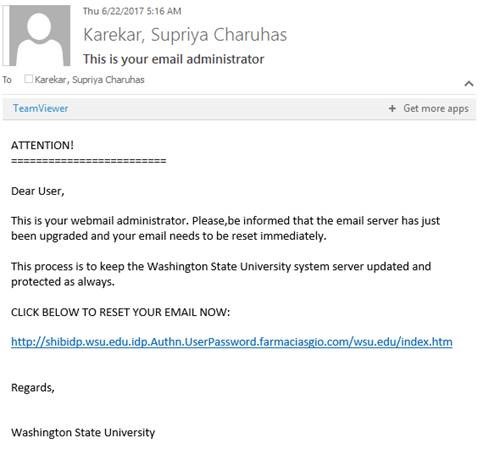
Please delete if you receive this.
=========================================